In this blog we will get to know How to Prevent Email Spoofing and Impersonation in Office 365.
Email spoofing and impersonation is a one of the form of cyber attacks in which the sender tries to be someone you know in order to get vital information out.
They can send email from different email addresses but the display name would be of someone who you know and trust, this makes it easier for the attackers to get access to the information by asking their targets.
These attackers sends email asking for immediate money transfer or asking to click on some links to fill vital information, etc.
Most of the targets of these attackers are employees of an company/business, as they pretend to be their CEO, COO, etc. in order to the information they want to steal.
The best way to prevent spoofing and impersonation is to check the source of the email, its sending emails address.
If the emails is received from CEO, CFO, COO, etc. then the email address of the sender should be of the same domain as the company’s and not from some external domain like gmail, yahoo, etc.
Microsoft provides protection for the Spoofing and Impersonation to protect specific domains and/or any users in your company but it requires respective licenses for it.
We can use mail flow rule to create a rule that could prevent these spoofing and impersonation emails from reaching the end users, for free.
Related article: How to Restrict Sender or Entire Domain From Sending emails in Office 365 | How to Perform Message Trace in Office 365
Steps on How to Prevent Email Spoofing and Impersonation:
We can create a transport rule for emails coming from outside of the organization with specific names in the from field.
We can then quarantine emails or block them, which matches the above conditions.
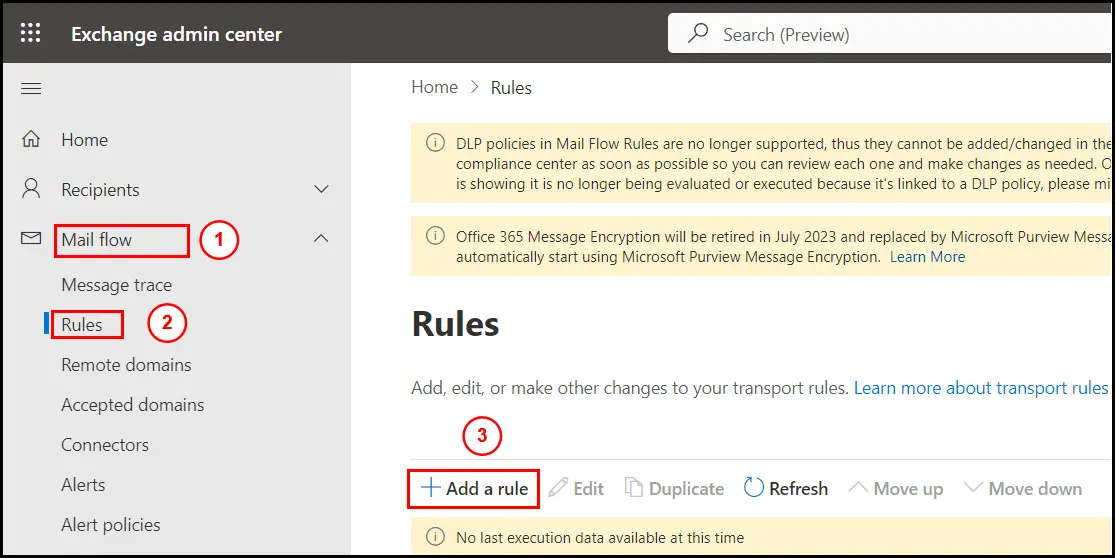
To create mail flow rule go to Exchange admin center and sign in with an Exchange admin or Global admin account.
Click on Mail flow > under Mail flow click on Rules and then click on Add a rule option:
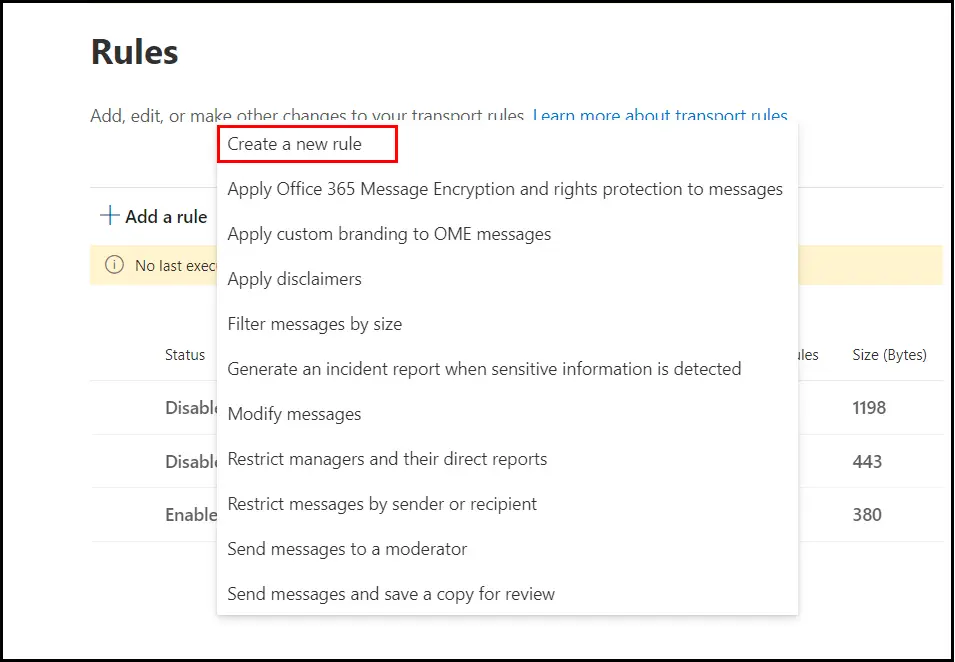
Click on Create a new rule option from the list of options:
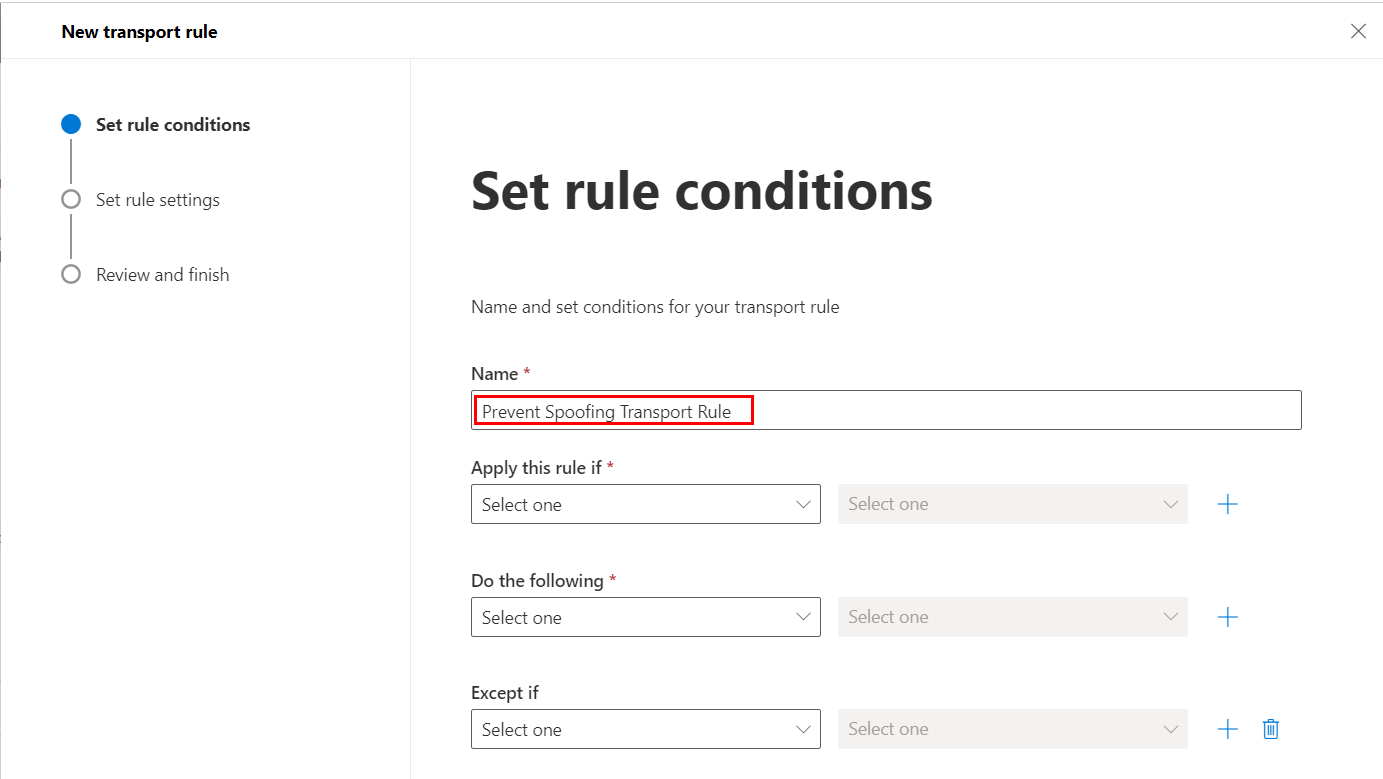
Rule wizard will open, in that Give the rule its Identifiable name:
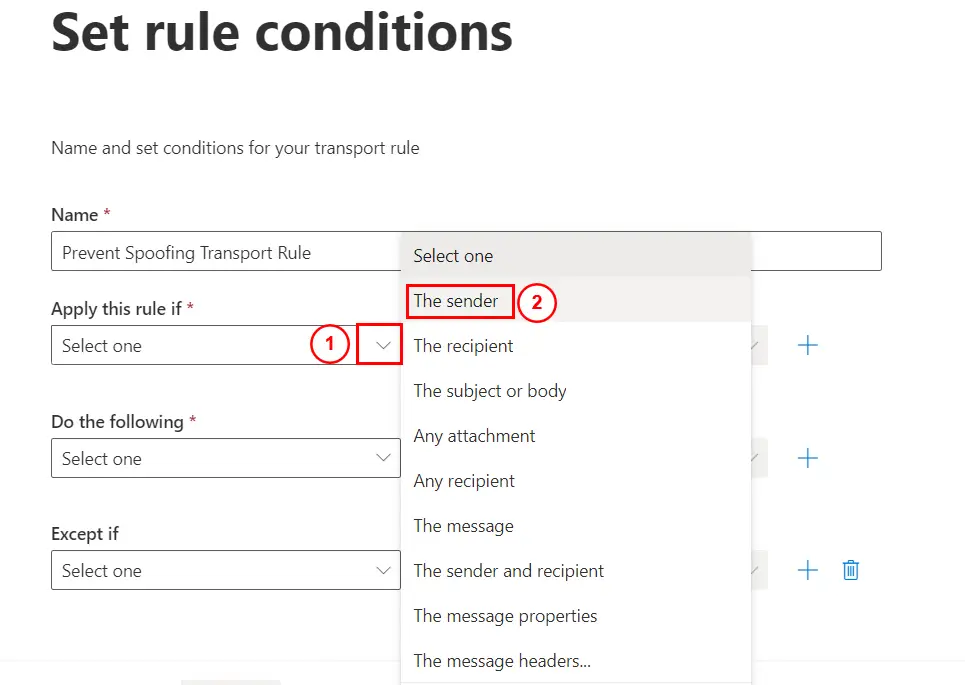
Under Apply this rule if option, click on the drop down and select The sender:
Then select the drop down on the right and then select is external/internal:
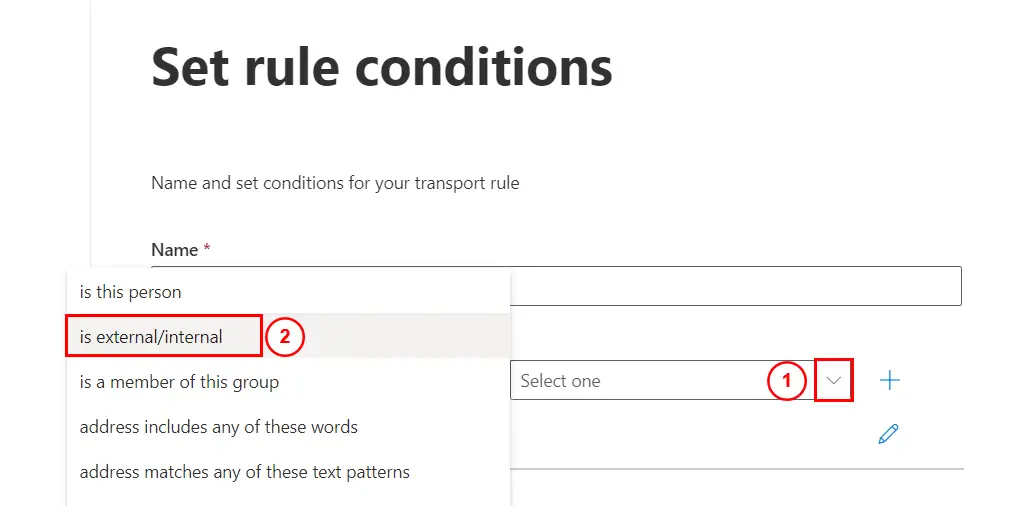
Click on Outside the organization from the drop down:
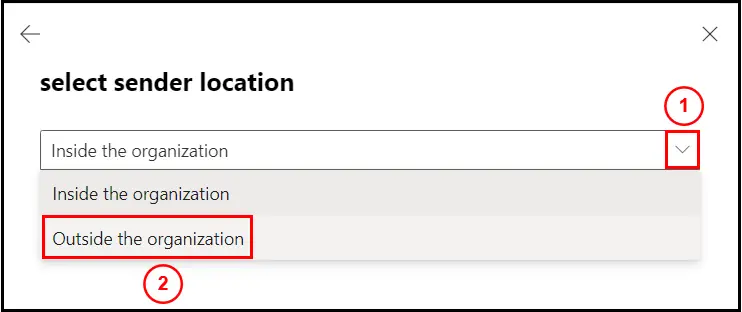
Once done it should look like this:
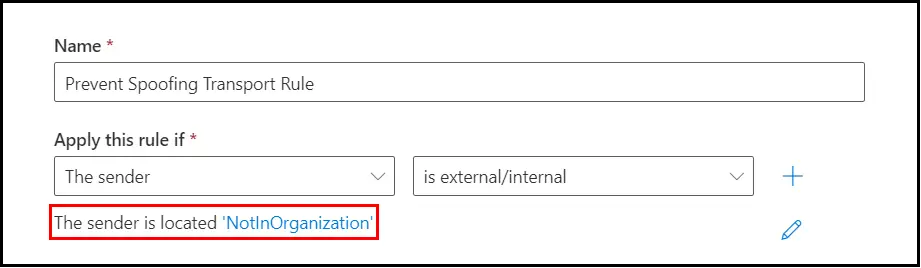
Now we will add one more AND condition by clicking on the plus sign:
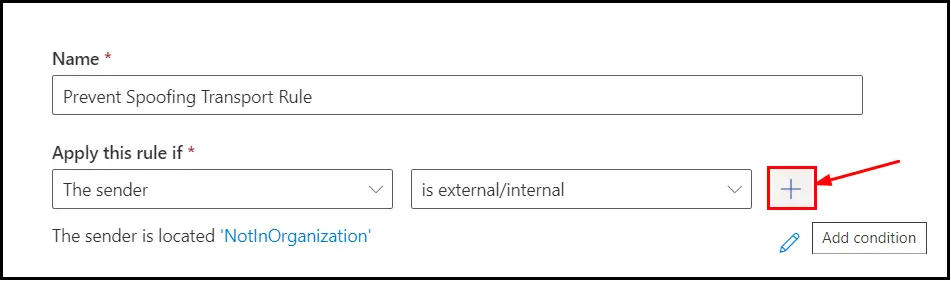
New condition block will appear as shown below:
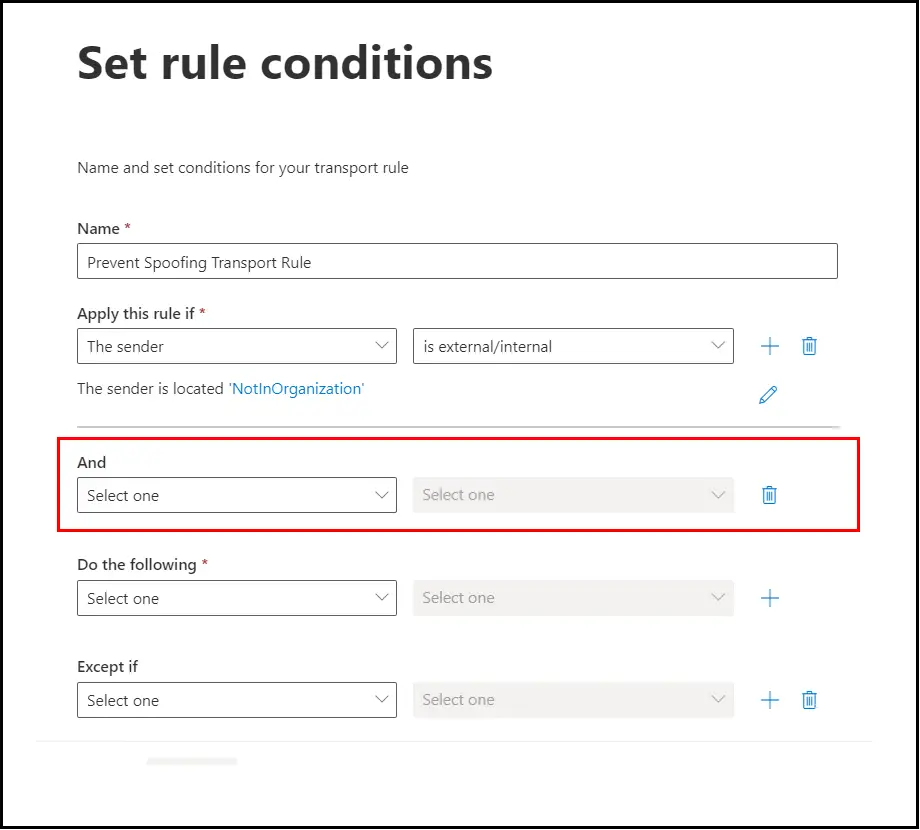
Click on the drop down and then select the option, The message headers:
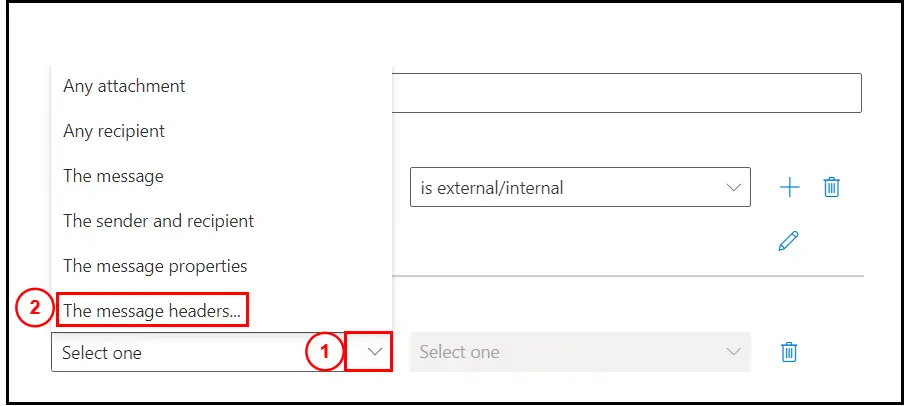
Click on the drop down beside it and then select, includes any of these words:
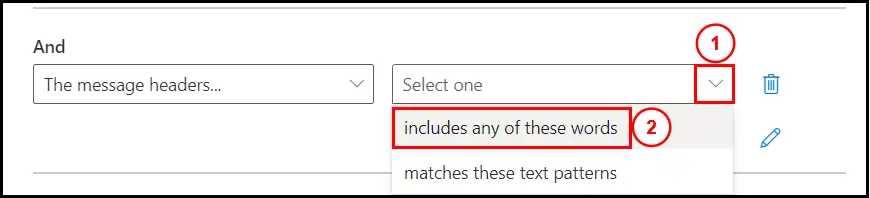
Now click on the Enter text as shown below:
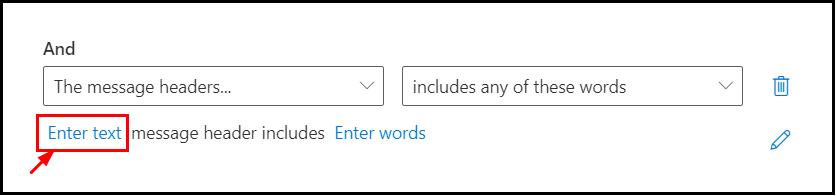
Specify header name as “from” and save it:

Now click on Enter words option:
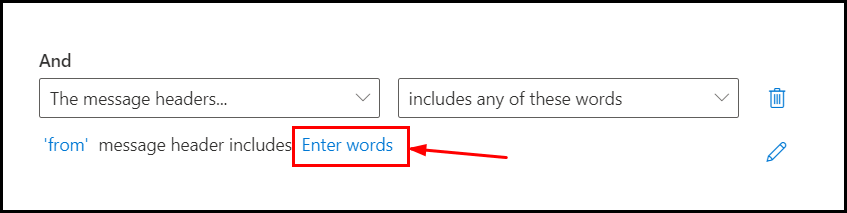
It will open the windows where you can specify the name of the people to prevent getting impersonated:
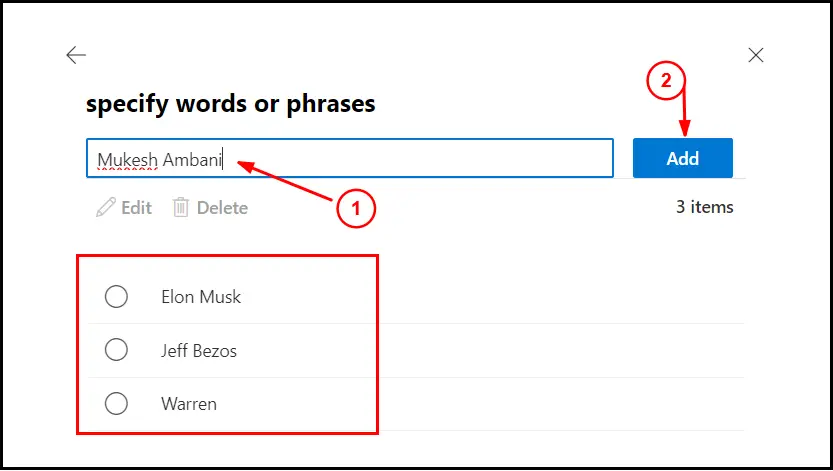
I would suggest to add users who has high authority or are from billing department, in your organization.
If you add first and last name in here, all the email coming form outside with the first and last name in the from field will be captured.
Keep in mind if the external email has for example Elon Musk Tesla in the from name, it will be captured as well.
Same is when you only add first name, all the external email with that first name and any last name will be capture by the rule.
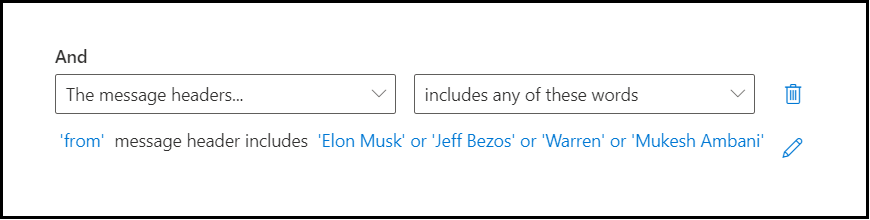
Once you have added click on Save:
Now we will have to mention, what to do with the email which gets captured by the rule, select the drop down under, Do the following:
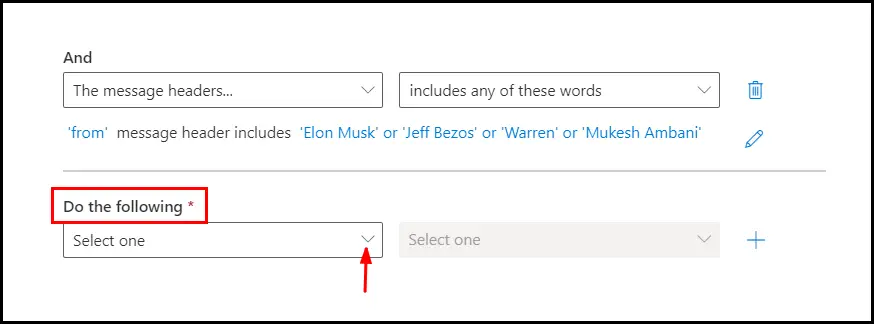
Select, Redirect the message to:
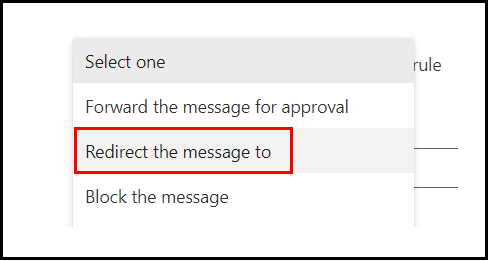
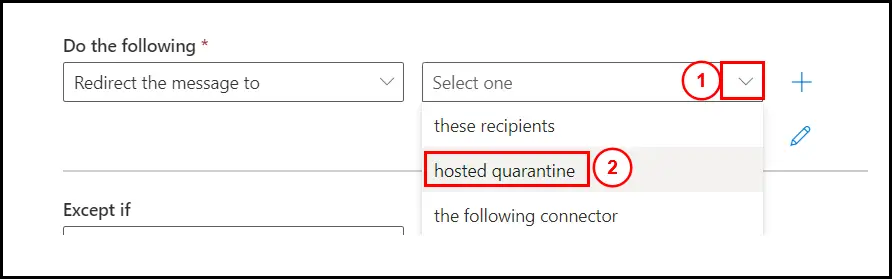
Select the drop down next to it, select hosted quarantine:
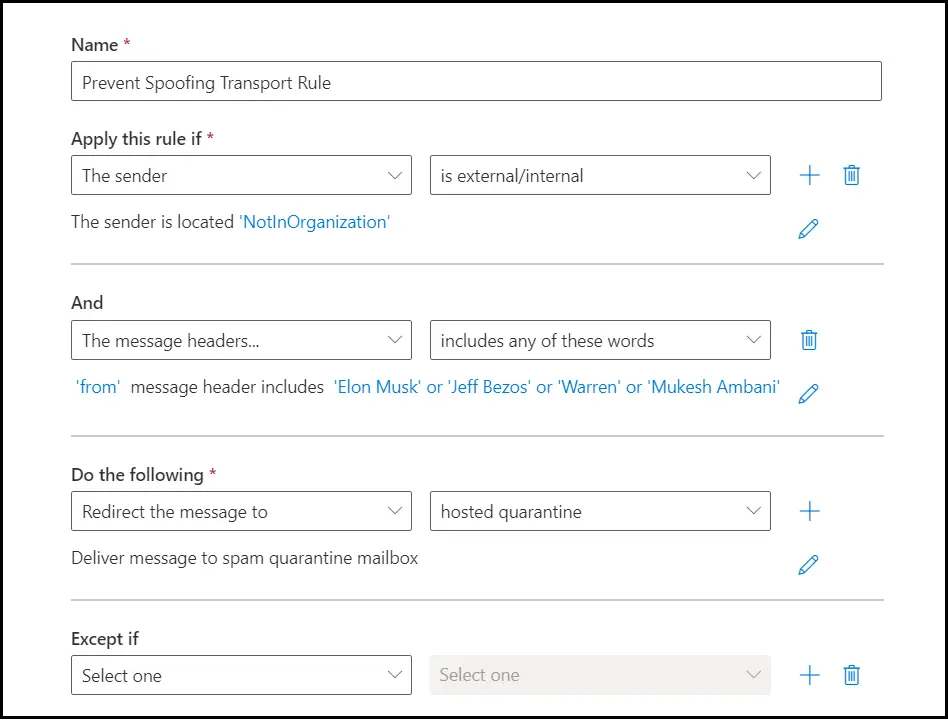
Once you have done all of the settings, the rule should look like this:
You can simply hit Next to complete the setup, no need to change any other settings:
Click on Finish:
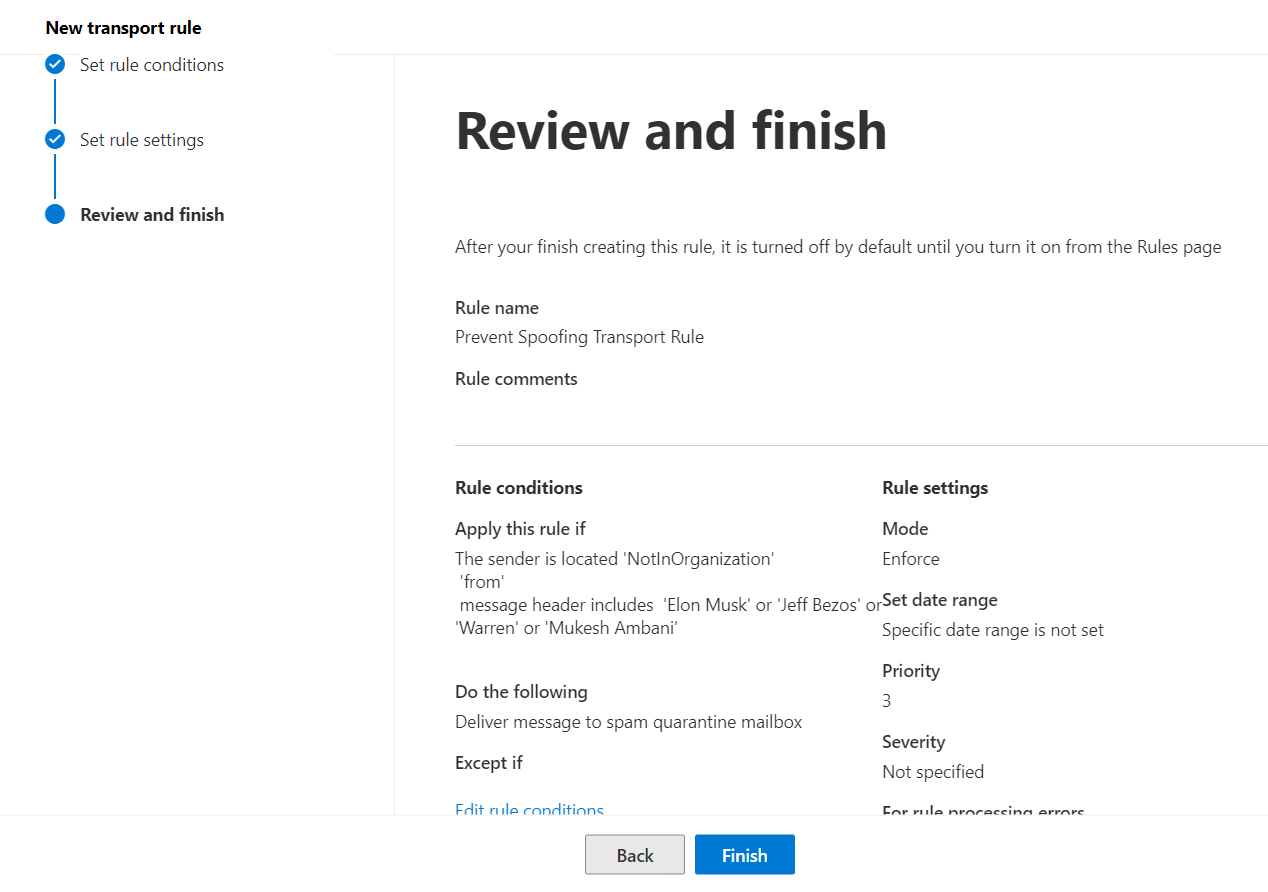
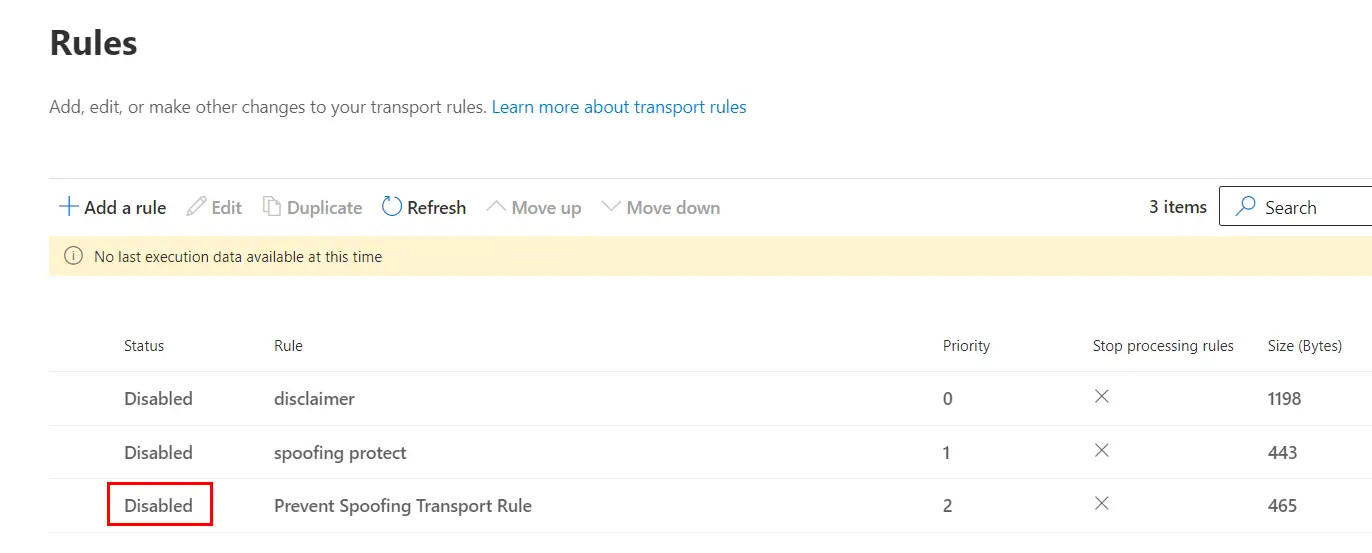
After the rule is created, it by default is Disabled:
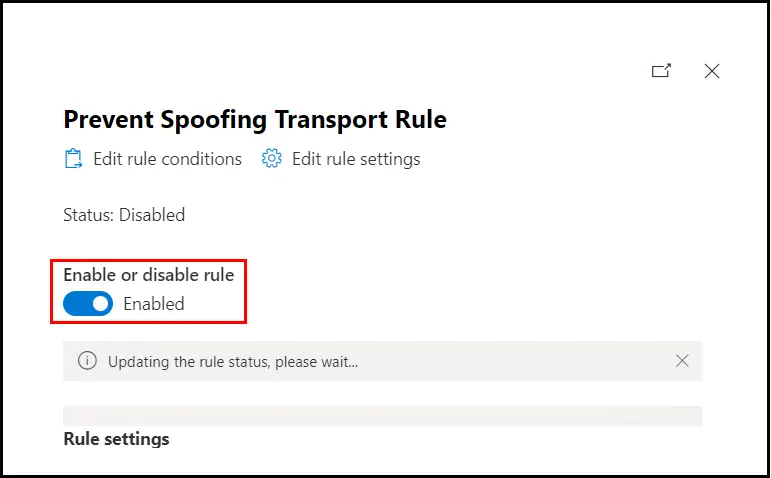
Click on it and then turn the toggle to Enable the transport rule:
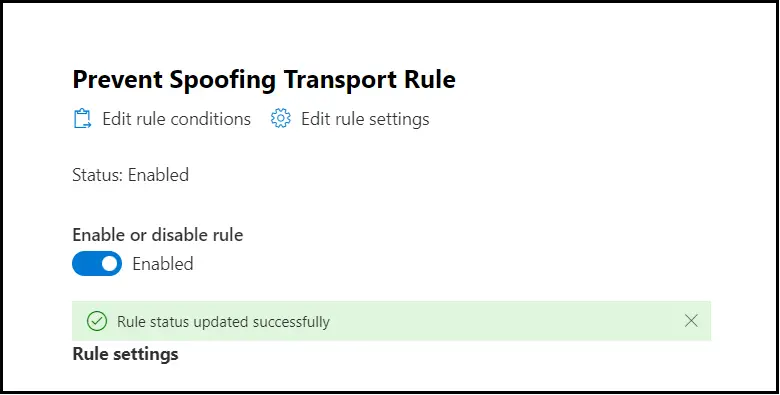
Once the saving is completed, you will see the following message:
Now all the External emails with those name in the from field will be moved to quarantine.
If the users has their personal external id, it will get blocked too, if you want to allow them, you can simply add them in the Except it condition in the rule, which we created.
Except if > the sender is > then type the complete external email address and save it.
To review the emails which has been quarantine, you can simply visit to the Quarantine tab in the security admin center using the link: https://security.microsoft.com/quarantine
It will show you all the emails quarantined for the past 30 days, by default.
By default emails are stored in quarantine for 14 days, after that they are deleted.
In this way we can create a transport rule to prevent Spoofing and Impersonation emails from coming through.
Do let me know if you have any question, in the comment section below.
Date: 24/10/2023
Author: Prem
Tag: How to Prevent Email Spoofing and Impersonation